The Alarming Rise of DeFi Hacks in 2024 and Why Automated Event Handling Is Crucial


In Brief
The DeFi industry faces significant security issues, with a Q3 2024 Web3 Security Report showing $463 million in stolen funds, highlighting the need for enhanced protocols.

According to the most recent Q3 2024 Web3 Security Report from Hacken and Extractor, the DeFi industry is still facing serious security issues. Even while the number of hacks has dropped to its lowest point in three years, the financial effect is still significant. In just 28 occurrences during the third quarter of 2024, an astounding $463 million was taken, underscoring the critical need for enhanced security protocols throughout the DeFi ecosystem.
95% of all stolen monies were lost permanently, according to the report’s conclusions, which is alarming given that in prior quarters, 50–60% of stolen assets were usually either recovered or frozen. This pattern emphasizes how crucial it is to put strong prevention measures and post-incident reaction plans into place.
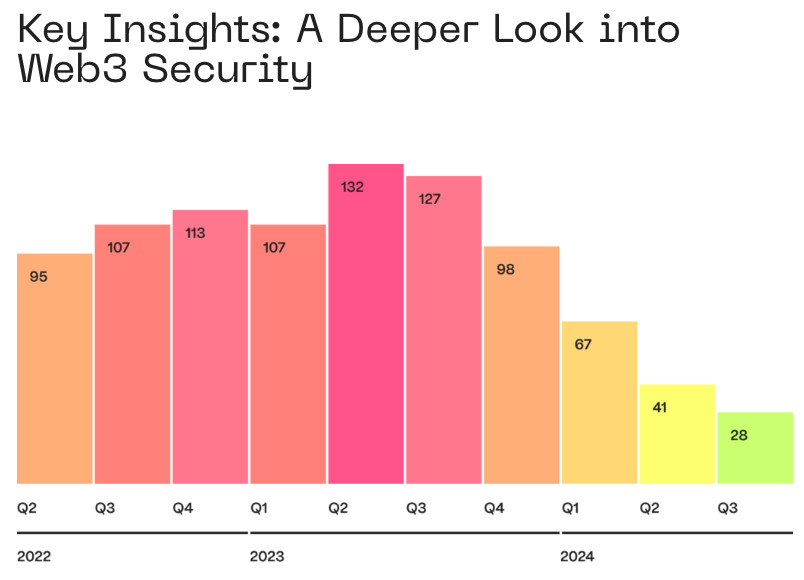
Photo: Hacken
Automated Event Handling: An Innovative Method
Automated incident response strategies are one of the most promising alternatives that the research highlights. With its innovative real-time attack detection and mitigation capabilities, this method may have avoided around thirty percent of all DeFi losses during the previous three months. This indicates the considerable influence such tactics may have on lowering vulnerabilities and safeguarding user assets—potential savings of over $25.6 million.
Several real-world examples demonstrate the efficacy of automated incident response. In one instance, identifying unusual withdrawals it might have stopped 17% of the $12 million hack on the Ronin Bridge. In another case, by immediately stopping contracts during a malicious proxy upgrade, it might have completely prevented Nexera’s $1.5 million loss. These instances demonstrate the effectiveness of automated reactions and real-time monitoring in drastically lowering financial losses before an assault has a chance to materialize completely.
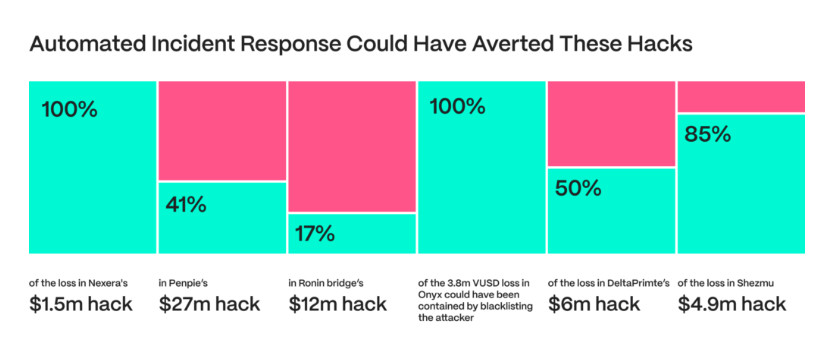
Photo: Hacken
DeFi initiatives should take into consideration the following actions in order to build an efficient automated incident response plan. They must first set up thorough monitoring systems that are capable of immediately identifying irregularities and possible threats. In order to do this, alarms must be put up for odd transaction patterns, abrupt activity spikes, or departures from typical smart contract behavior.
Second, initiatives ought to create and put into practice predetermined reaction methods. These protocols ought to specify the precise steps that must be done in reaction to certain risks. For instance, putting contracts on hold automatically when questionable behavior is noticed or momentarily stopping sizable transactions when they reach particular criteria.
Third, it’s imperative that these automated methods be regularly tested and improved. It is imperative that incident response tactics are updated and refined on a regular basis to ensure their effectiveness as the DeFi environment changes and new attack vectors appear.
Finally, initiatives ought to think about combining human supervision with automated incident response systems. While automation can offer quick first answers, more complicated scenarios and the need to make nuanced judgments in the face of possible security concerns sometimes require human experience.
Audits, Bug Bounties, and Upgrades
Even while automated incident response techniques provide a great deal of security, they work best when paired with other preventative security measures. In-depth smart contract audits are crucial, the research says, especially before introducing updates or new versions. Because many vulnerabilities result from hurried or insufficiently tested updates, thorough auditing procedures are crucial.
One further essential element of a thorough security system is bug reward programs. Through providing incentives for security researchers to properly disclose vulnerabilities, initiatives can effectively leverage the combined knowledge of the broader community. This methodology not only facilitates the detection of possible vulnerabilities but also cultivates a security-aware culture throughout the DeFi ecosystem.
The paper also emphasizes how contract upgrades must be managed carefully. Because smart contract vulnerabilities frequently surface after new versions are released, it is important for projects to establish rigorous procedures for testing and verifying updates before the deployment. To find any problems before they can be exploited, this may need slow rollouts, protracted testnet testing, and several levels of review.
Improving private key security is a crucial component of lowering vulnerabilities. Utilizing hardware wallets and secure key management programs may greatly lower the possibility of unwanted access and offer virus protection. Projects should think about introducing multi-signature wallets for crucial processes and instruct users on the best key management procedures.
Taking Care of the Core Causes: Rug Pulls and Access Control
Access control compromises are the most hazardous kind of attack, according to the Q3 2024 Web3 Security Report, with losses from them that are twice those from all other attacks put together. This emphasizes how crucial it is for DeFi protocols to have strong access control measures in place. The least privilege concept should be applied to projects, guaranteeing that each system component has the least amount of access required to carry out its duties.
The survey also observes a change in the rug pull scam environment. On systems like Base, Tron, and Solana, the number of launches of memecoins has increased while standard rug pulls have decreased. This pattern implies that con artists are changing the way they operate, concentrating on low-value coins that imitate rug pull behavior without exhibiting any indications of authentic activity. DeFi platforms and users must both exercise caution and impose more stringent screening procedures for the introduction of new tokens in order to counter this.
Creating a DeFi Ecosystem That Is More Secure
It is impossible to overestimate the significance of strong security measures as the DeFi industry develops. The Q3 2024 Web3 Security Report is a plan for enhancing security and a wake-up call at the same time. Through the use of automated incident response plans, comprehensive audits, bug bounties, and careful management of updates and access control, DeFi projects may dramatically lower their attack surface susceptibility.
In addition, the industry as a whole has to make an effort to promote a security-aware culture. This include teaching users about potential hazards and best practices in addition to putting technological solutions into effect. It will be essential for projects, security companies, and the general public to work together to find vulnerabilities and fix them before they can be exploited.
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.
More articles

Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.


















































