Match Systems Guide: Protecting Yourself from Scams in the TON Ecosystem


In Brief
Match Systems’s report on the TON ecosystem highlights its vulnerability to fraudulent activities, highlighting tactics used by scammers and strategies for mitigating threats.

Andrei Kutin, the CEO of Match Systems, has released a comprehensive report on the TON ecosystem, available on the company’s website. Here, we summarize the key takeaways from the research, offering valuable advice to help users stay safe within this rapidly evolving ecosystem.
The TON ecosystem was initially praised for its decentralized nature and seamless connection with Telegram, but it has unfortunately become a prime target for various fraudulent activities. These scams not only harm users financially but also damage the ecosystem’s overall credibility. In their in-depth review, Match Systems details the tactics scammers use, the reasons behind the increasing fraud, and how these threats can be mitigated.

Photo: Match Systems
Scammers, previously active in the Ethereum blockchain, have shifted to TON due to its comparatively weaker security measures. They exploit TON’s vulnerabilities with tactics like wallet drainers, phishing attacks via Telegram, fake airdrops, and impersonation schemes. Unlike Ethereum, which has implemented stronger defenses, TON lacks advanced security tools, making it a lucrative target for criminals. Integration with Telegram adds another layer of vulnerability, resulting in even greater losses in 2024.
Techniques like phishing, social engineering, and technical exploits—such as fake mini-apps—are common strategies. Automated attacks using wallet drainers exploit user permission gaps, making them particularly dangerous.
The picture below provides a schematic of the types of crime prevalent in the TON ecosystem.

Photo: Match Systems
Moreover, scammers often launder the stolen funds through decentralized exchanges, making it nearly impossible to recover them. To defend against these risks, users must stay vigilant, adopting strong security measures, while the TON ecosystem urgently needs to strengthen its protection mechanisms.
Hackers’ Tools in the TON Ecosystem
In the TON ecosystem, cybercriminals rely on various services to build an infrastructure for their illegal activities. These include domain registration, SEO manipulation, traffic generation tools, VPNs, and proxy services. Each of these components plays a vital role in enabling scammers to remain anonymous while scaling their operations. The infographic below illustrates how these tools are employed to create and sustain a network of illicit activities within the TON ecosystem.
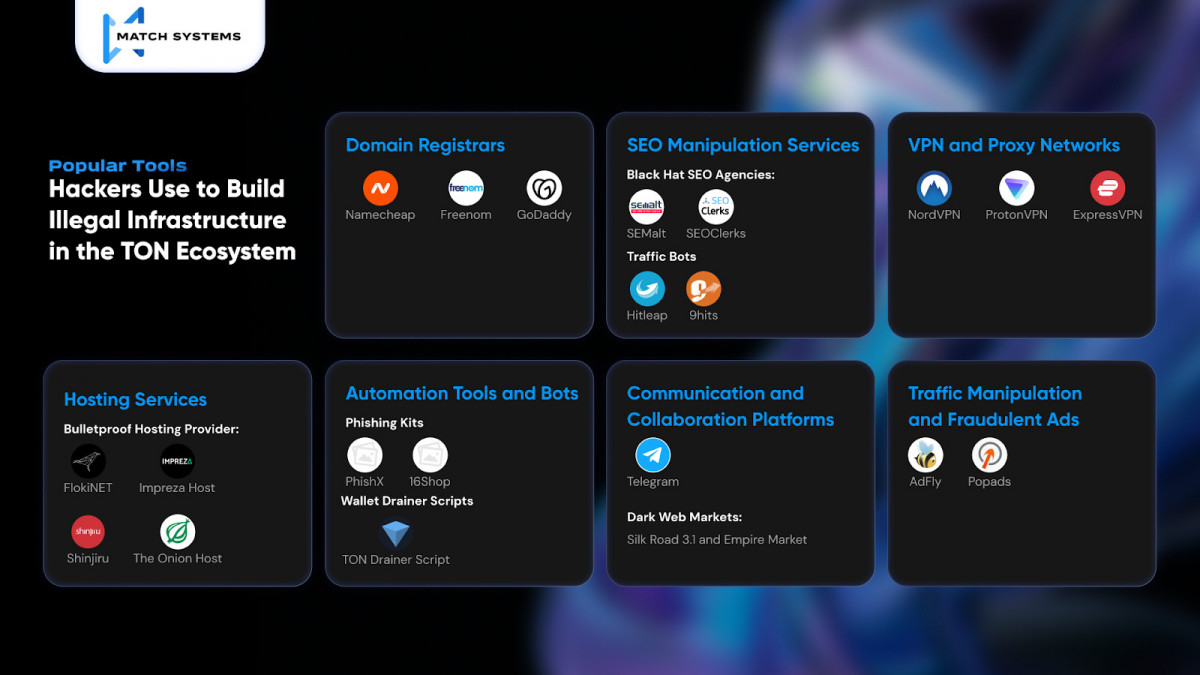
Photo: Match Systems
Once hackers steal cryptocurrency, laundering the funds to hide their origins becomes a critical step. This process usually involves the use of crypto mixers and privacy coins, which are designed to make transactions harder to trace. These methods allow criminals to convert stolen funds into usable assets while minimizing the risk of being caught.
Here are the ways hackers usually launder the stolen funds in the TON ecosystem.

Photo: Match Systems
How to Protect Yourself in the TON Ecosystem: A Practical Checklist
Match Systems has compiled a checklist designed to help users avoid falling victim to scams in the TON ecosystem. By following these steps, you can lower your risk of being targeted:

Photo: Match Systems
If you’ve fallen victim to a scam, report the incident immediately using Match Systems’ “Report on Crypto Incident” Telegram bot. Acting quickly could improve the chances of recovering your stolen assets.

Photo: Match Systems
By incorporating these safety practices and utilizing Match Systems’ tools, users can significantly reduce their vulnerability to scams within the TON ecosystem.
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.
More articles

Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.


















































