Circle STARKs Unveiled: Buterin’s Latest Innovation Promises to Solve the Blockchain Scalability Trilemma


In Brief
Vitalik Buterin introduced Circle STARKs, a cryptographic mechanism to enhance blockchain safety and effectiveness, overcoming previous STARK implementation drawbacks.

Vitalik Buterin, a co-founder of Ethereum, developed the cryptographic mechanism known as Circle STARKs to increase the safety and effectiveness of blockchain. In order to overcome the drawbacks of earlier STARK implementations, this invention introduces major enhancements to the STARKs framework.
The Growth of More Specific Domains in Cryptography
Smaller cryptographic fields, especially Mersenne31, are the foundation of Circle STARKs and represent a major shift from the larger 256-bit fields frequently used in previous STARK protocols. Larger fields were more secure, but they also frequently led to slower proving rates and computational inefficiencies. High-performance gains result from switching to Mersenne31.
However, restricted fields have a restricted range of possible values, which might lead to security flaws. Buterin’s team uses extension fields in conjunction with many random tests to overcome this issue. By extending the range of values an attacker would have to guess, this method benefits from smaller field performance while erecting a computational obstacle to preserve the validity of the protocol.
Because Mersenne31 can be used to perform effective arithmetic operations using existing 32-bit CPU/GPU operations—arithmetic operations can be roughly 1.3 times more productive than those in other smaller field protocols like BabyBear—adding and multiplying can be accomplished with a straightforward bit shift activity and commonly used opcodes for handling high-order bits.
Fast Reed-Solomon Interactive Oracle Proofs of Proximity (FRI)
FRI, an essential step in guaranteeing that functions are polynomial to a certain extent, is implemented using Circle STARKs. By adding an additional layer of security to the protocol, this solution preserves cryptographic integrity by rejecting proofs for non-polynomial inputs.
Circle STARKs optimizes the FRI method for efficiency. It arranges polynomial evaluations using a modified reverse bit order, which improves the protocol’s space efficiency and enables more powerful Merkle proofs. The folding structure utilized in Circle STARKs is especially intended to be complemented by this ordering mechanism.
The domain reduction procedure in traditional FRI entails squaring the elements of the multiplicative subgroup using a two-to-one map. But Circle FRI presents a fresh strategy. It functions on a set of points (x, y) that fulfill the prime modulus equation x^2 + y^2 = 1 mod p. This structure allows for a novel folding procedure that preserves the required qualities for fast proof creation.
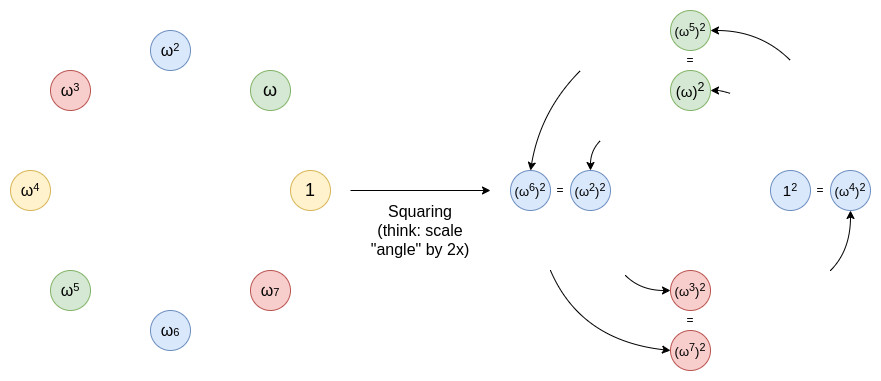
Photo: Vitalik Buterin
The initial step in the Circle FRI method is to collapse all of the points onto a single line. Next, the domain size is decreased by selecting random linear combinations. After every round, the set size is essentially cut in half because a new map is used. Until the polynomial degree is low enough for direct verification, this process is repeated.
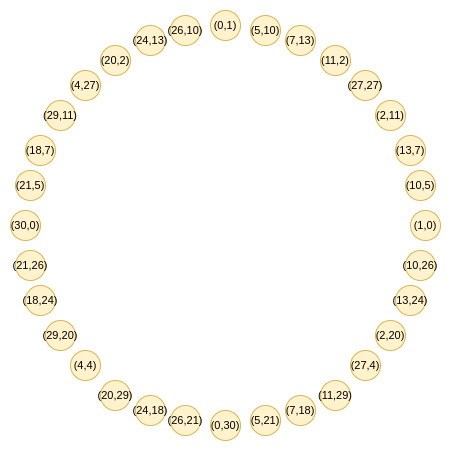
Photo: Vitalik Buterin
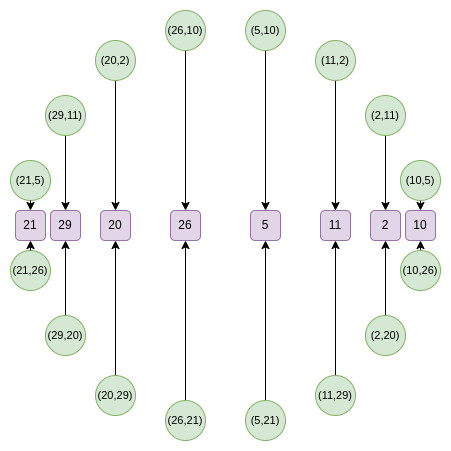
Photo: Vitalik Buterin
Productivity and Developer’s Accessibility in Balance
Crucially, Buterin points out that, in contrast to standard STARKs, Circle STARKs don’t impose much more complexity on developers. Since the protocol encapsulates much of the underlying mathematical complexity, developers may work with Circle STARKs without having to completely understand all of the minute mathematical nuances.
Additionally, the protocol presents “exotic FFTs” (Fast Fourier Transforms), which strike a compromise between readability and efficiency. Circle FFTs provide better performance without being as complicated as elliptic curve FFTs, yet they are still usable by academics and developers. The blockchain community’s acceptance and further development of the protocol may depend on its accessibility.
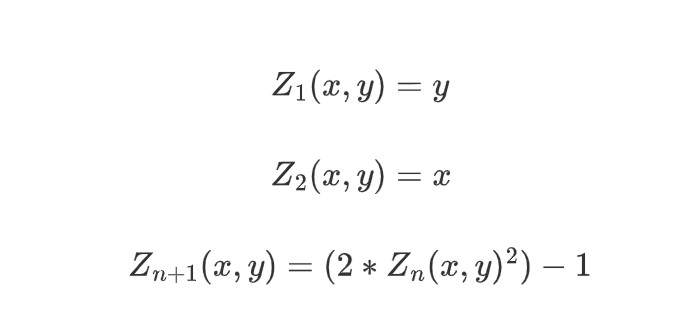
Photo: Vitalik Buterin
Round Polynomials “modulo” the circle equation x^2 + y^2 = 1 can be conceived of as polynomials on what mathematicians refer to as a Riemann-Roch space, on which FFTs work. This structure preserves the mathematical features required for safe cryptographic proofs while enabling efficient calculations.
Implications for Blockchain Scalability and Security
Circle STARKs tackle critical issues related to security and scalability on the ledger. The increasing use of blockchain in several industries has led to a growing demand for protocols that can manage larger transaction volumes while upholding robust security assurances.
The efficiency improvements that Circle STARKs provide may have a big impact on how much electricity blockchain networks use. The protocol has the potential to lower the computing resources needed for cryptographic proofs, hence improving the environmental sustainability of blockchain technology. This element is especially crucial in light of the rising worries over the energy usage of cryptocurrencies that rely on proof-of-work.
The use of Circle STARKs in the field of zero-knowledge proofs may result in more effective applications. Since zero-knowledge proofs are essential for a lot of privacy-preserving applications, this enhancement might lead to a larger acceptance of blockchain solutions focused on privacy. Rapid proof generation and verification might open up new applications for privacy-preserving systems like supply chain monitoring, identity management, and decentralized finance.
Additionally, Circle STARKs may be advantageous for layer-2 scaling approaches. The protocol may improve the performance of rollups and other layer-2 technologies by increasing the efficiency of cryptographic proofs, which might result in increased transaction throughput and decreased costs for blockchain users.
Impact on Blockchain Architecture
The blockchain architecture may be impacted by the launch of Circle STARKs. It could be possible to incorporate more complicated logic directly on-chain as cryptographic proofs get more efficient, which might lessen the requirement for some layer-2 scaling solutions. This may cause a change in the architecture and use of blockchain systems, opening the door to new kinds of decentralized applications that were previously unfeasible because of processing limitations.
More effective STARKs, for instance, would make it possible to carry out on-chain privacy-preserving calculations that were previously prohibitively costly. This may create new opportunities for decentralized finance applications, enabling the implementation of more sophisticated financial instruments while protecting user privacy.
Addressing the Scalability Trilemma
The blockchain scaling trilemma—the difficulty of simultaneously attaining scalability, security, and decentralization—is being addressed in a better way with the introduction of Circle STARKs. Circle STARKs help make blockchain systems more scalable without sacrificing security or requiring greater centralization by enhancing the effectiveness of cryptographic proofs.
It’s crucial to remember that Circle STARKs by themselves do not resolve every facet of the scalability problem. Complementary technologies and strategies will still be required to handle other issues including state expansion and network latency.
Potential Applications Beyond Blockchain
Although Circle STARKs are mostly addressed in relation to blockchain technology, there are other possible uses for them. Other applications of cryptography and secure computing may benefit from the efficiency gains provided by Circle STARKs.
For example, more effective STARKs might allow more complicated collaborative calculations while preserving anonymity in the realm of secure multi-party computation. This may be useful, for example, in medical research when several people must compute sensitive data while keeping the underlying facts secret.
Circle STARKs have the potential to facilitate more effective zero-knowledge proofs of identifying traits in the context of digital verificatiom, hence paving the way for more privacy-preserving systems. Everything from digital IDs issued by governments to internet authentication may be affected by this.
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.
More articles

Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.


















































