Blockchain’s Democracy Under Siege: How Buterin and Cornell Researchers Are Engineering the Future of Incorruptible DAO Voting


In Brief
Ethereum co-founder Vitalik Buterin and Cornell University academics are exploring strategies to reduce bribery assaults, a significant risk in decentralized governance, as these systems encourage decentralization but also pose potential exploitation risks.

Co-founder of Ethereum Vitalik Buterin has been investigating strategies to lessen bribery assaults, one of the biggest risks to decentralized governance, with a group of Cornell University academics.
The Emergence of DAOs and the Issues with Their Governance
Decentralized autonomous organizations provide an alternative way to decision-making and structure of operations. DAOs seek to establish open, democratic platforms where tokenholders directly influence the organization’s operations and future course by utilizing blockchain technology. However, as these systems proliferate and gain value, they also present themselves as desirable targets for exploitation.
The lack of a central authority and the collaborative decision-making of token holders on governance are one of the fundamental tenets of DAOs. Although this paradigm encourages decentralization, it also leaves room for possible misuse in the form of bribery assaults. In these kinds of situations, bad actors may provide token holders with financial incentives in return for casting a certain vote, thus undermining the democratic mechanism that DAOs are designed to support.
The Way Bribery Attacks Work
It’s important to look at the potential means of these attacks in order to comprehend the seriousness of the bribery danger. Typically, an attacker would write a smart contract that pays token holders who cast votes that support the attacker’s objectives. This compromises the integrity of the voting process by creating a “dark marketplace” where votes can be purchased and sold.
The problem derives from the fact that most existing voting systems don’t have safeguards against token holders disclosing their voting patterns to outside parties. This feature is essential for bribery assaults since it enables the attacker to confirm that the voter they bribed fulfilled their half of the agreement.
Trusted execution environments (TEEs) can also be utilized by skilled attackers to manipulate the timing and manner in which voting keys are employed. Even after taking a bribe, attackers might essentially force token holders to vote in particular ways by encumbering the secret keys within these safe settings.
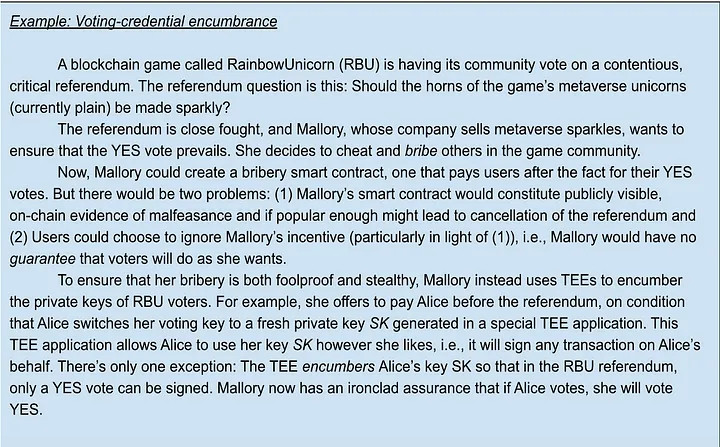
Photo: IC3
The Project for Research
Realizing how serious this issue is, Cornell University academics led by PhD candidates together with Vitalik Buterin, have been working on creating solutions. Their work focuses on “proofs of complete knowledge” (CK), a novel cryptographic notion that attempts to plug the gaps that allow bribery attacks to occur.
The group’s efforts advance the idea of cryptography’s proof of knowledge. Even while proof of knowledge enables one party to demonstrate ownership of confidential information without disclosing it, there is still a little vulnerability that may be used against them. This discrepancy results from situations in which the prover does not directly own the secret information; instead, it is kept via trusted hardware or other external processes.
Proofs of Complete Knowledge: A Possible Remedy
The goal of the notion of proof of complete knowledge is to prove that data belongs to specific, identifiable individuals. This strategy might greatly lower the possibility of bribery attempts by guaranteeing token holders total control over their voting keys.
The researchers have determined that there are two main approaches to applying proofs of complete knowledge:
TEE-based Approach
To demonstrate that a voter is the owner of a key and has unrestricted access to it, a trusted execution environment is used. Crucially, the token holder has all control over how the key is used since they may still take it out of this context. This method guarantees that the key stays under the control of the voting system’s own TEE, even in the event that an attacker tries to lock it away.
ASIC-based Restriction
The second strategy uses application-specific integrated circuits (ASICs), which are similar to those used in Bitcoin mining, to restrict keys. Sending a key to an ASIC—which does not have a TEE environment—allows the user to access the key still and has proof that the ASIC utilized it. This successfully hinders efforts at vote rigging by preventing the key from being used in a TEE.
Practical Implications and Challenges for Proofs of Complete Knowledge
It’s crucial to remember that proofs of comprehensive knowledge are still at the prototype stage, even though the research into them shows promise. The group has developed a study prototype of a “dark DAO” that can enable vote buying, proving that bribery assaults are a serious danger to current DAOs. However, there are a number of obstacles to turning this research into workable, broadly applicable solutions.
Finding a balance between usability and security is one of the main challenges. Enforcing complicated cryptographic methods would make it harder for regular users to participate in DAOs, which might undermine the intention of inclusive, wide governance. Adopting these anti-bribery systems widely will depend on finding the ideal mix between strong security measures and user-friendly interfaces.
Unintended repercussions are another factor to take into account. Like with every security solution, there’s always a chance that skilled attackers may figure out new methods to get past the defenses. It will take ongoing study and development to keep ahead of changing dangers.
The Role of Education and Community Awareness
In addition to focusing on technological solutions, the blockchain community as a whole has to work together to create awareness and educate others about the bribery problem. It is imperative that token holders comprehend the significance of their involvement in upholding the integrity of decentralized systems, as well as the possible ramifications of engaging in vote-selling operations.
Technical protections might be significantly enhanced by community-driven initiatives that stigmatize bribery attempts and encourage ethical voting behavior. Creating a culture of accountability and care among DAO members may act as a strong disincentive for people who could be persuaded to trade votes for quick money.
Research on proofs of comprehensive knowledge and other anti-bribery techniques is a significant step in the progress of decentralized government. But it’s evident that this is only the start of a lengthy journey. Strong, safe voting mechanisms will become increasingly necessary as DAOs continue to expand in both quantity and significance.
In order to improve these ideas and apply them to practical situations, academics, developers, and the larger blockchain community must continue their collaborative efforts. Peer review and open communication will be essential in spotting such flaws and boosting these systems’ resilience.
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.
More articles

Victoria is a writer on a variety of technology topics including Web3.0, AI and cryptocurrencies. Her extensive experience allows her to write insightful articles for the wider audience.


















































